Multi-line SHA1 hash generator, SHA1 encryption
This tool is used to encrypt your text items (up to 50,000), where each item is on a separate line into multiple SHA1 hash results at once.
If your items are on a single line, please use this text splitter to split them into multiple separate lines.
What is this multi-line SHA1 hash generator?
It is a free online multi-line SHA1 hash generator that was made by the 'PU Tools' developer team. The number of uses is unlimited without any registration requirement.
It will use your text items, where each item is on a separate line as multiple inputs which are used to encrypt into multiple SHA1 hash results at once.
It does allow your maximum input items that are up to 50,000 each time. If your requirements are larger, you can split them and use this tool multiple times.
If your items have one or multiple empty lines, and you don't want this hash generator to encrypt them, please check the 'Remove empty lines' option.
It's fair and treats an empty character as a single character (*).
If you don't enter anything, it means you want to enter an empty character. Of course, we respect your decision.
The empty character in SHA1 is 'da39a3ee5e6b4b0d3255bfef95601890afd80709'.
To find the corresponding SHA1 hash, please enter your text into the form above.
Below are the test vectors of SHA1 encryption:
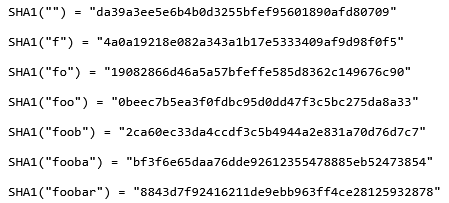
Explanation of the point (*):
As a programmer, I usually have to work with characters in the command line, database, and the user's input includes alphabets, numbers and other special characters.
So, all the characters are very important to me. I have to work with them seriously to avoid errors occurring. That's why this tool is the same as me, and it doesn't have the right to ignore any type of character.
Thus, if you want it to encrypt an empty character. Just leave the input box empty or give an empty line in your list of items.
About the SHA1 encryption.
SHA1 is an acronym for 'Secure Hash Algorithm 1'.
It is a one-way hashing algorithm. There isn't any direct method for its decryption.
It was designed by the National Security Agency (NSA) and published by the National Institute of Standards and Technology 1 (NIST) in 1995 as a successor to SHA-0.
It is used extensively for many security protocols and applications.
It generates a fixed-size 160-bit (20-byte) hash value from an input text of any length. There are 40 hexadecimal characters in a SHA1 hash.
Given the same input, SHA1 always produces the same hash value.
Although once considered secure, SHA1 is now considered insecure for most security applications due to discovered vulnerabilities, most notably the possibility of hash collisions. A hash collision occurs when two different inputs produce the same hash value.
In general, SHA1 is thought to be more secure than MD5. Because it generates a longer hash (160 bits as opposed to 128 bits), it is more impervious to brute-force attacks.
For programmers, if you want to increase the security of SHA1, you can add salt to the beginning or end of the value you want to encrypt. The stronger the salt you add, the more secure your output will be. Example of a strong salt: 6k#N3^1bT0J8.
--------------------------------------------------
Above is basic information about SHA1. If you want to discover more, please visit: SHA1 on Wikipedia.
Related Tools
Our Popular Tools
Encryption Tools
Encoding Tools
Decoding Tools
Text Tools
Data Tools
Date and Time Tools
Finance Tools
